abstract
INDDoS is a simple volumetric DDoS victim identification strategy built on top of ==BACON Sketch== to identify the destination IPs contacted by a number of source IPs greater than a threshold, in a given time interval, completely in the data plane.
problem
given

estimate
the number of flows(identified by different $key{src}$ keys) that contact the destination host identified by $key{dst}$ in Tint
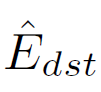
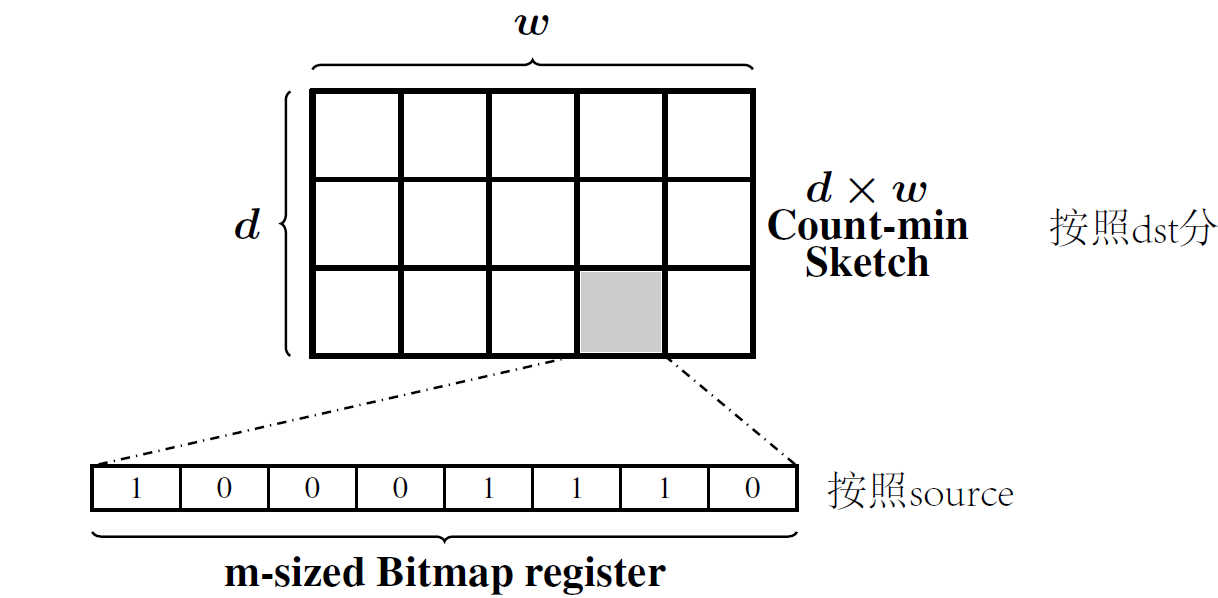
BACONsketch
data structure
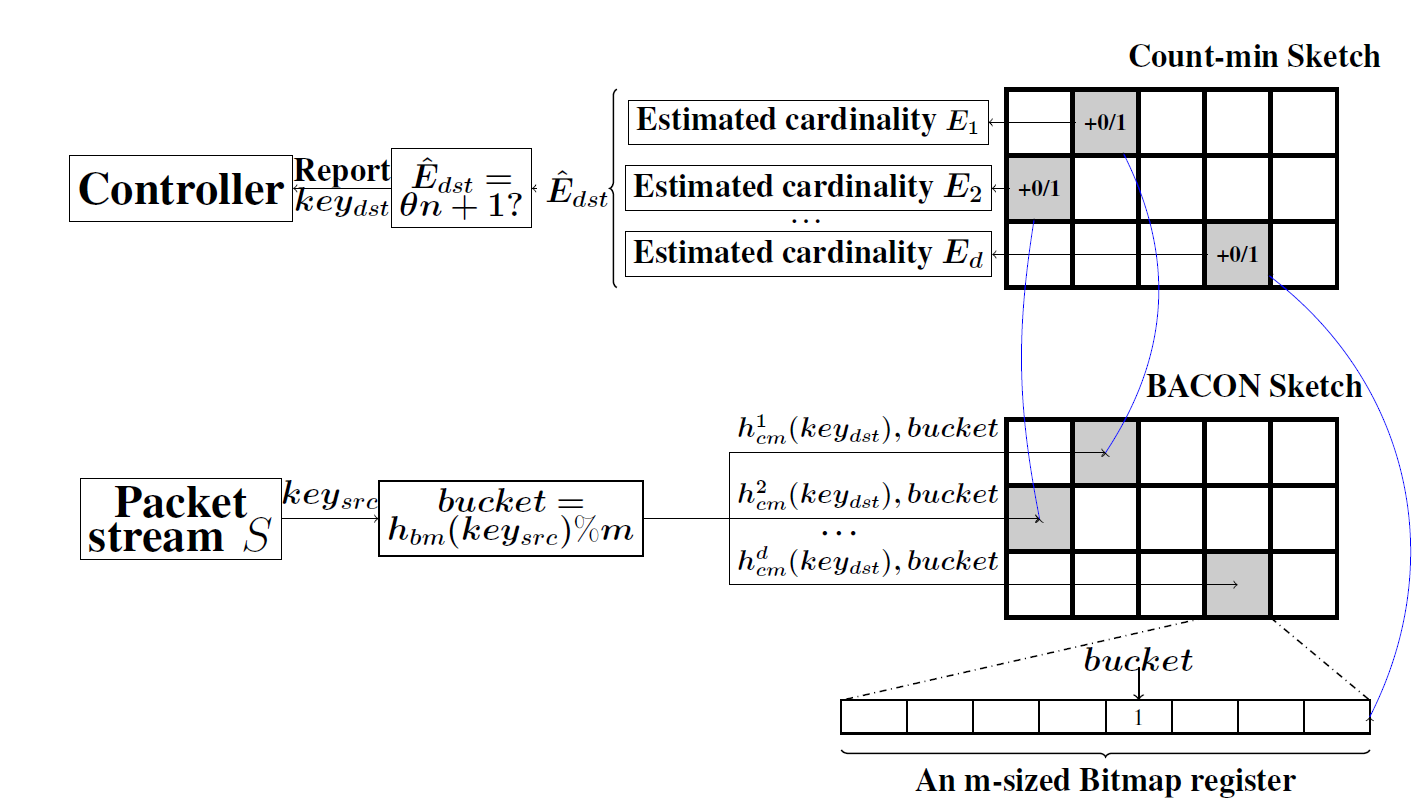
update&query algorithm

BACON for DDoS
given

return
- all destinations $key{dst}$(DDoS victims), that satisfy $E{dst}$>$\theta$ within time interval $Tint$
implemention
实际实现中使用一个小的CMsketch 直接储存BACON中每个bucket中1的个数,查询的时候查询这个小CMsketch即可。
related work
spreadsketch
数据结构:
- combination of Multiresolution Bitmap and Count-min Sketch
实现:
- Multiresolution Bitmap 需要log计算来估计cardinality,P4不支持log计算,只能在bmv2上实现
- 对同一个metadata运算2次,在硬件中不能有多余两次arithmetic operations。但是这里需要多余2次
entropy based DDoS detection
- 基于熵的DDoS检测只能alarm,而不能识别受害者。
- 本文基于flow的DDoS检测不仅可以alarm,还能知道手滑这,减轻对目标节点影响
experiment
on Tofino
💡emm
这篇文章灵感可能来源于spread sketch,只是把里面的复杂bitmap换成了direct bitmap
里面还介绍了P4结构来水页数
- 还是未发表工作