title
In-Network Volumetric DDoS Victim Identification Using Programmable Commodity Switches
motivation
- whenever a metric requires to set some global, network-wide threshold, then an accurate estimation of the total traffic volume is of paramount importance
- 但是会有多个交换机重复记录同一数据包
- most assume that each packet is counted by a single programmable switch on its path through the network,
- one could mark counted packets, but such a solution is inherently insecure since an attacker could pre-mark its packets, avoiding detection
Goal
given

return
Distinct flow numbers $\hat{n}_{tot}$
Average flow size $\hat{R}_{tot}$
Total packets number$|\hat{S}_{tot}|$(最终goal)
algorithm
在这项工作中利用的 HLL 的联合属性确保多个 HLL 寄存器,例如 Mm 和 Mn,可以合并到一个寄存器中 Mmn = Mm$\bigcup$Mn 来统计独立更新了 Mm 和 Mn 的数据包流的流基数,即$\hat{n}Mm\bigcup M{n}$,避免重复计算。
Distinct flow numbers
$\hat{n_i}$是单个交换机$M_i$查询HLL得到的不同流数量的估计
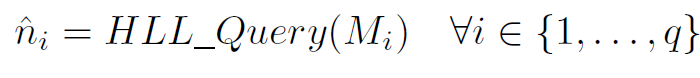
将q个交换机中top-k交换机的hyperloglog求并集,估计得到总共有多少个不同流。
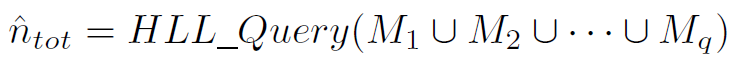
根据下式,topk交换机就可以估算所有交换机的distinct flow counts。
- Average flow size
$\hat{Ri}$是(交换机i在$T{int}$时候的packet num/单个交换机$M_i$查询HLL得到的不同流数量的估计),得到交换机i average packet num
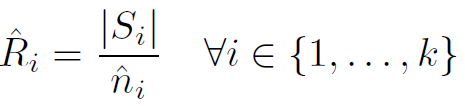
求q个交换机中top-k的交换机中估计得到的$\hat{n_i}$ 的平均值
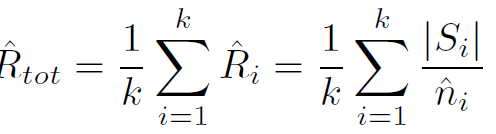
- Total packets number
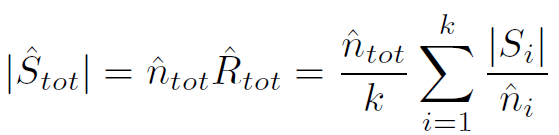
evaluation
- sensitive to many…
- 在敏感度分析中用上了他之前的deployment的工作,也提到了apaptive threshold
💡
- sensitive to flow key types, time interval width, network topology, …不鲁棒,受太多因素的影响了
- 提醒了我再deployment那个工作中需要注意长尾分布和全是大流的情况下,对总体流量的估计是不准确的,会低估