0. motivation
- entropy可以检测flow cardinally的变化,急剧下降代表有DDoS
entropy方法需要log和exp和浮点运算
P4不支持division, logarithm, exponential function calculation
1. goal
- to estimate network traffic statistics directly in P4 programmable switches,
- normalized entropy
- flow cardinality
- with the final goal of using them as building blocks to accurately and timely detect DDoS attacks
2.0 network traffic entropy
fi is the packet count of the incoming flow with flow key i
|S|tot is the total number of processed packets by the switch during Tint
n is the overall number of distinct flows
- d is the base of logarithm(chose 2)
![]()
公式变形一下:
![]()
方框中定义为Sum(|S|),这一部分比较复杂是迭代求解的。
后面实现主要分为两个部分:
Update counter计算|S|tot
迭代计算Sum(|S|)
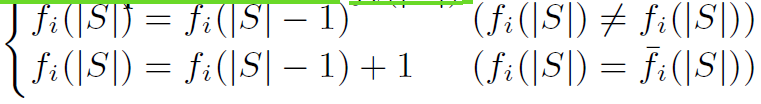
如果来的是这个流的包就+1, 如果不是就不更新
用当前fi的值替换过去一个时刻的fi的值
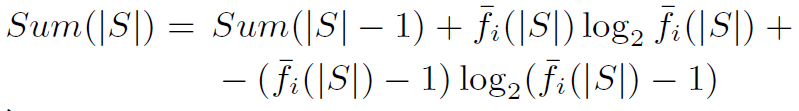
对上面式子做一下化简
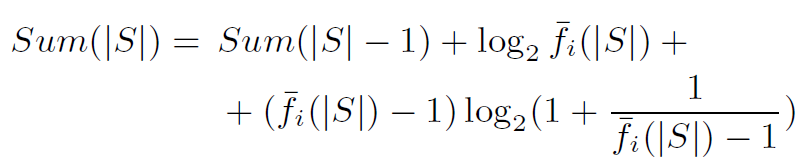
根据L’Hopital’s rule, 化简最后一项的为1/ln2
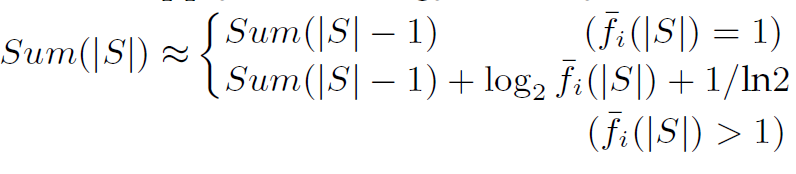
最后计算entropy的时候都改成2的幂次方的形式, 例如

得到最后的entropy化简为:
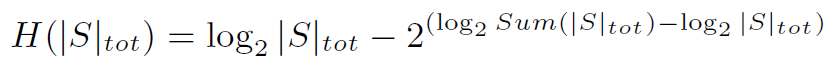
和最开始对比一下:
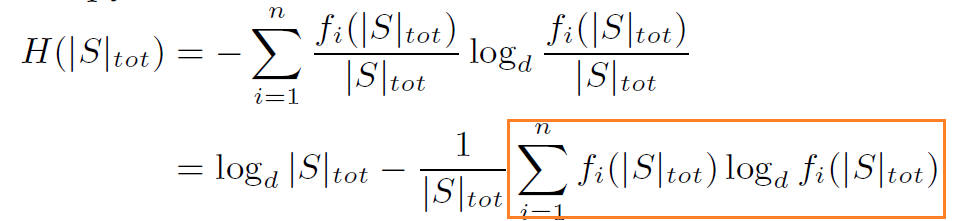
考虑一些情况,分类
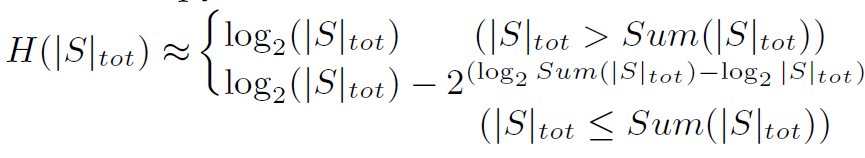
在Tint估计Entropy H(|S|tot)
大的sketch是CM
小sketch是用来储存每个flow id对应的Sum(|S|)
P4loglog计算n
好计算最后的Normally Entropy
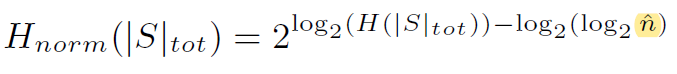
![]()
2.1 Flow cardinality estimation: P4LogLog
2.2 Normalized traffic entropy estimation: P4NEntropy
2.3 DDoS Detection
![]()
3 Adaptive threshold setting
![]()
![]()
experiment
- normalized entropy 不能在tofino上实现
- flow cardinality 可以在tofino上实现
- Mininet+bmv2